DTEK is transforming itself to meet new challenges.
The threat landscape is rapidly expanding, requiring adaptation and changes in approaches to protecting information and systems. DTEK implements a comprehensive approach to information security management.
The main objectives of information security are:
- To implement a systematic approach to information security management at DTEK, taking into account DTEK’s strategic goals, risk-based approach, requirements of applicable laws and best international standards and practices
- To ensure the confidentiality, integrity and availability of information and data processed at DTEK, in accordance with the requirements of applicable law
- To raise Employees’ awareness of current information security threats to reduce risks associated with the human factor
- To ensure cybersecurity of DTEK’s IT and OT infrastructure in accordance with applicable laws and international information security standards.
The principles of information security include:
Continuous improvement
information security management is based on the PDCA (Plan-Do-Check-Act) cycle — a continuous process of development and improvement.
Compliance
implementing information security measures and tools in accordance with the current requirements of the legislation on information security and information protection.
Informing
ensuring timely and sufficient information to stakeholders on matters concerning information security.
Structure and Regulation
the defining, describing, and standardising of information security business processes for the purpose of uniformity and application.
Comprehensiveness
a systematic approach to ensuring information security throughout the entire life cycle of software and information systems development and implementation.
Minimum privileges
granting users, systems, and processes the minimum necessary rights to access information assets sufficient to properly perform their functional duties.
Detection and Response
implementing measures to localise and neutralise information security incidents to detect threats in a timely manner and strengthen the protection of DTEK’s information assets.
Continuity
the continuity of information security measures and means is ensured taking into account the continuity of business processes and the consequences of possible emergencies.
Awareness raising
conducting periodic events aimed at raising the awareness of DTEK employees about information security and cybersecurity (cyber hygiene). Checking the level of awareness and assimilation of materials.
Confidentiality
The protection of information and data processed at DTEK is a priority. The protection of restricted information and provision of access to such information is carried out in accordance with the requirements of the law.
To achieve its information security objectives, DTEK implements a set of organisational and technical measures, as well as security tools and methods aimed at protecting information assets from unauthorised access, use, privacy breach, modification, or destruction. The implementation takes into account the recommendations of ISO/IEC and NIST standards. The achievement of information security objectives is regularly monitored. If necessary, external auditors are engaged to conduct such an assessment.
Approach to the implementation of information security
To achieve its information security objectives, DTEK implements a set of organisational and technical measures, as well as security tools and methods aimed at protecting information assets from unauthorised access, use, disclosure, disruption, modification, or destruction. The implementation takes into account the recommendations of ISO/IEC and NIST standards.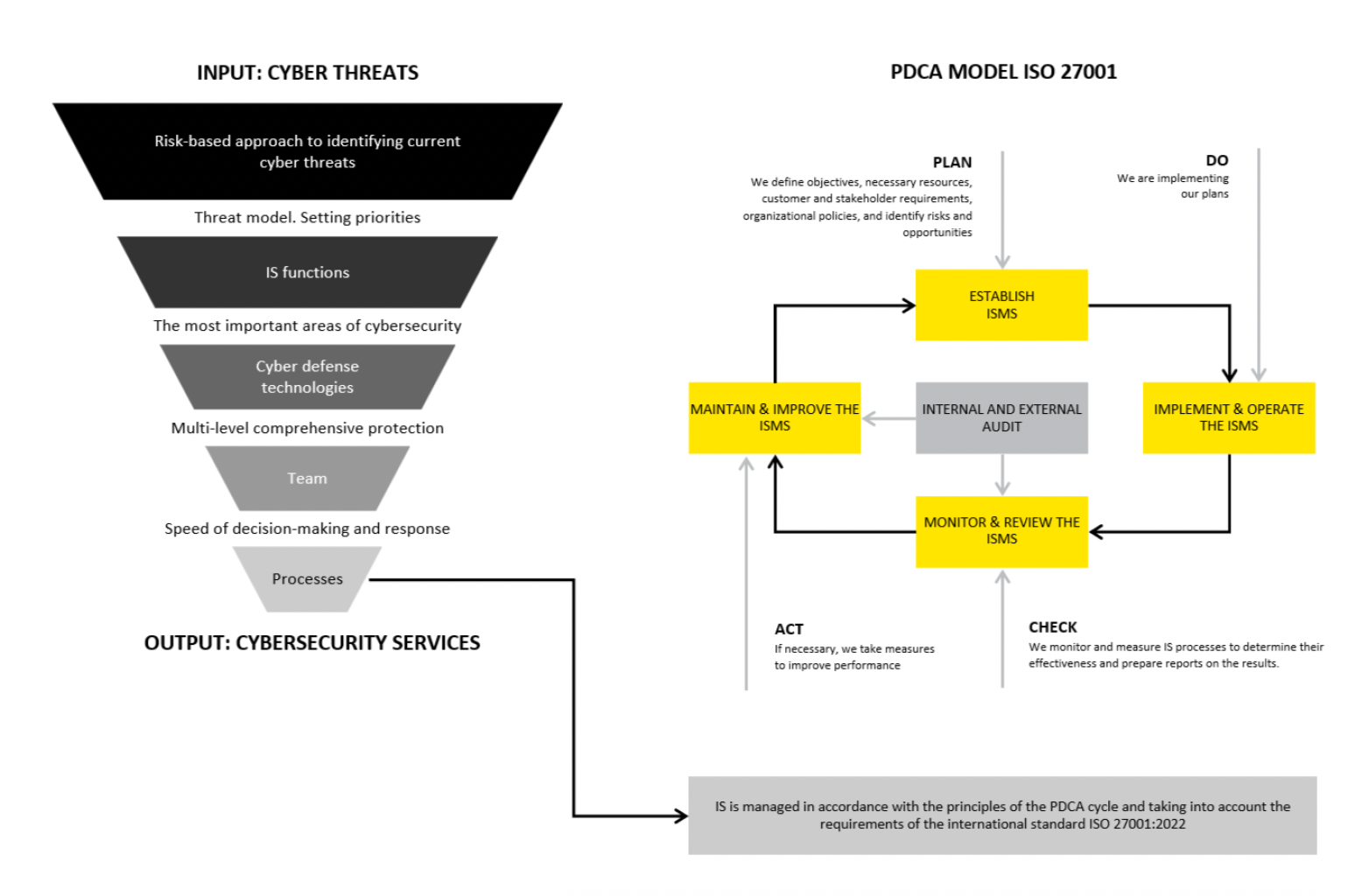
DTEK takes a risk-based approach to information security and a systemic-oriented (process-based) attitude toward operations.
High-level cyber security framework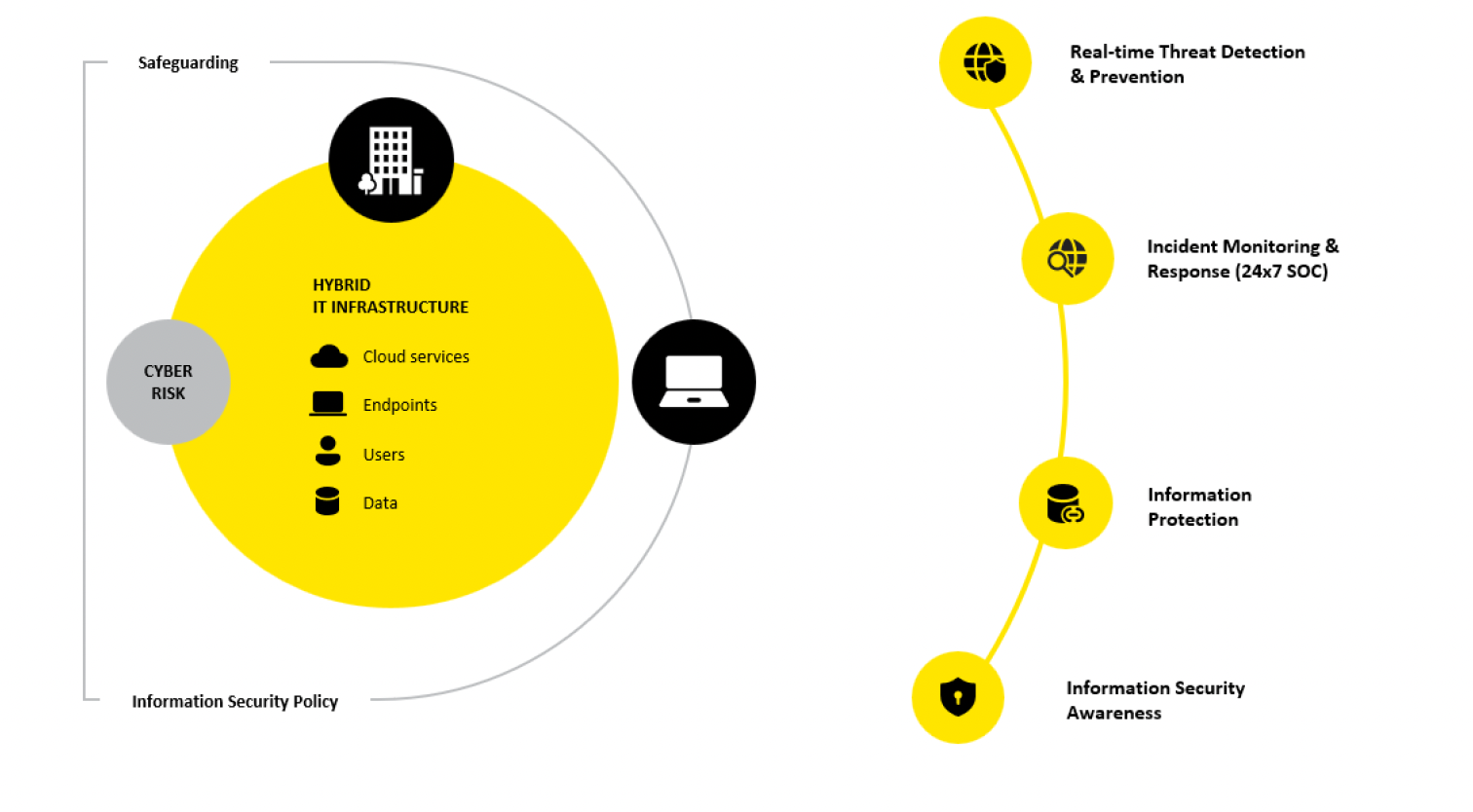
In order to manage information security risks, controls are being implemented to improve the protection of DTEK’s information assets:
- Organisational controls controls to set up the most important information security business processes and document them.
- Technological controls information technology-related controls.
- Human resources controls implementing HR controls to ensure compliance with information security requirements and rules.
- Physical controls controls concerning safe areas and the protection of equipment.
DTEK’s comprehensive approach to ensuring cyber resilience is based on 4 key areas:
1. Real-time threat detection and prevention
- Ensuring the confidentiality, integrity, and availability of the Company’s information resources and assets through a wide range of modern information security systems, including:
- Technologies to detect and prevent intrusions into the Company’s information network;
- Software solutions to protect servers, workstations, and virtual environments from malicious code;
- Multifactor authentication tools for access to the Company’s critical information resources;
- Automatic detection of vulnerabilities in the Company’s information systems and their prompt elimination;
- Monitoring the correctness of cloud security policy settings;
- Passing periodic independent assessments (PEN tests) for critical services.
2. Incident monitoring and response (24х7 SOC)
Monitoring of events in the IT infrastructure and prompt response to information security incidents.
Highly trained professionals provide real-time threat detection and monitoring of suspicious activity through the SIEM system 24 hours a day, 365 days a year.
DTEK interacts with specialised experts and cyber centres both in the energy sector and at the national level.
3. Information protection
Protecting confidential information of the Company and its counterparties is a priority for DTEK. To ensure the security of the Company’s and its counterparties’ information, DTEK uses various mechanisms to protect confidential information and control access thereto, including non-disclosure agreements (NDAs).
The Company makes every effort and is constantly working to improve its approach to the security of confidential information, taking into account current trends and threats to ensure proper protection of confidential information and personal data.
4. Information security awareness
Developing cyber hygiene skills among DTEK employees to reduce information security incidents.
DTEK has implemented mechanisms for regularly informing employees about modern types of information security threats and current information security rules to foster a responsible attitude of employees to information security and to ensure that they consciously comply with information security requirements and rules. Mandatory information security training materials are regularly updated to enhance knowledge of existing and emerging cyber threats.
